If you have digital assets, following best security practices is one of the top priorities. One of the best ways to do this is with two-factor authentication (2FA). But what is 2FA in crypto, exactly? Keep reading and find out.
[key_takeaways]
- Two-factor authentication (2FA) is a verification over a separate channel. It requires both a password and a second form of verification, like biometrics or a one-time code.
- 2FA adds extra security, protecting against unauthorised access and fraudulent transactions.
- Biometric verification, like fingerprint or facial scans, offers convenience and high security by confirming identity with unique physical traits.
[/key_takeaways]
What is a two-factor authentication (2FA)
Two-factor authentication is exactly what it sounds like: authentication that demands two methods (factors) to confirm the account owner's identity.
This method aims to stop unauthorised users from accessing your wallet or exchange account with just a stolen password. The 2FA consists of two authentication factors:
- Something you know (e.g., a password)
- Something you have (e.g., a hardware token)
- Something that the user is (e.g., biometrics)
Therefore, even if someone knows the password, they still need the second factor to access your crypto assets. This makes it harder for attackers to break in.

How does 2FA work in crypto?
Imagine 2FA as a double lock. First, you have the password that you enter while logging. This part is usual for any account.
The second phase is a little more complicated. You need to confirm your login using a second factor. Typically, it's a one-time code from an authenticator app or sent by SMS or email. This code confirms the user's ownership of the device or account.
The second factor is usually time-sensitive and changes for each login procedure. This makes it difficult for attackers to access an account, even if they have the user's password. This two-step verification greatly boosts the security of crypto accounts.
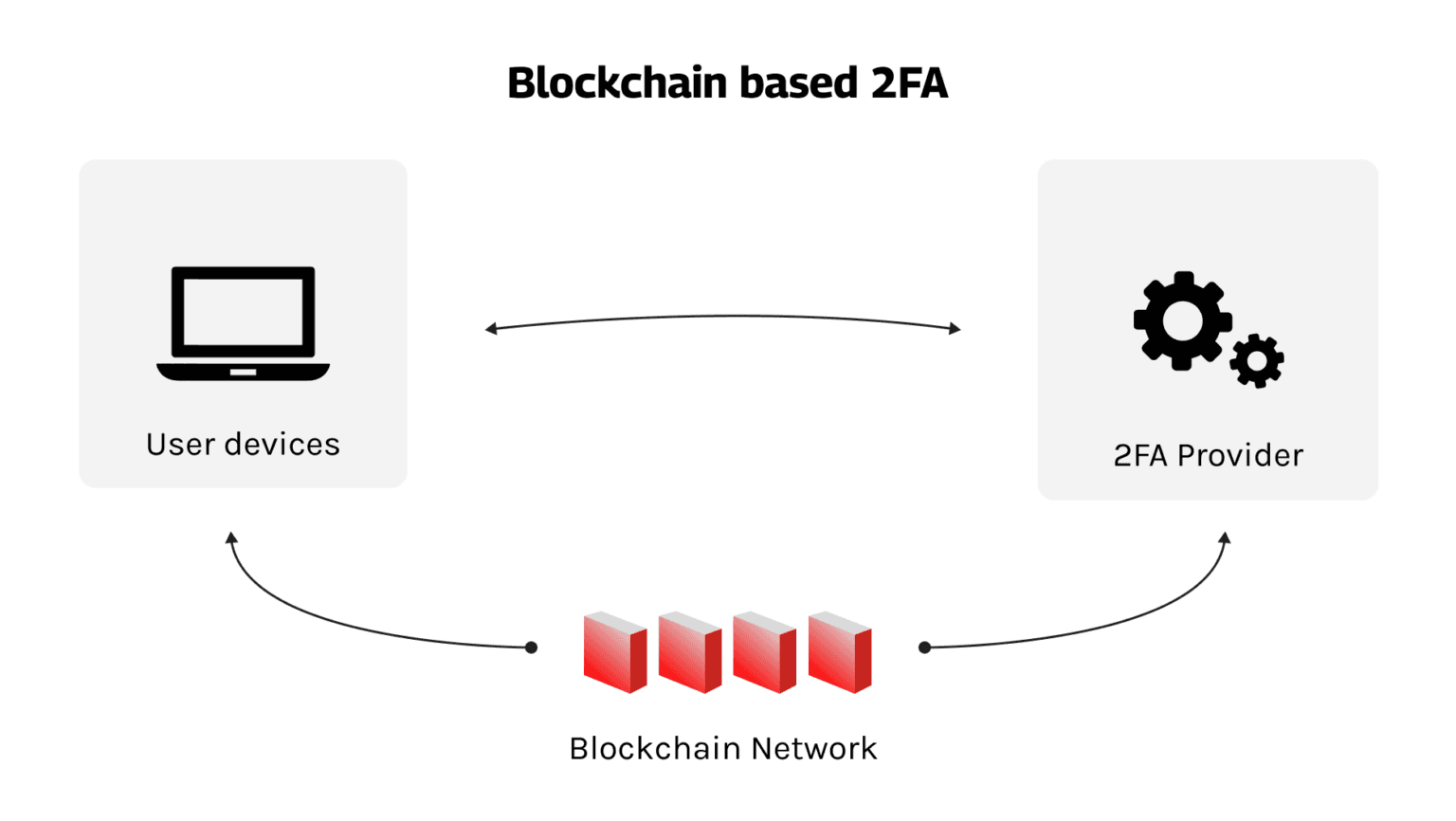
Technically, in a blockchain-based 2FA system, user devices are authenticated by a third-party provider through the blockchain network. Each party securely stores endpoint information and activates 2FA to generate a second-level password.
This system can operate publicly or within a private network with a third-party API call.
Why is two-factor authentication (2FA) important in crypto?
Two-factor authentication (2FA) is crucial for securing crypto accounts and assets due to their irreplaceable nature and potential unauthorised access, hacking attempts, and regulatory compliance issues.
Using 2FA adds an extra layer of security to protect cryptocurrency accounts and transactions, greatly reducing the risk of unauthorised access and fraud.
What are the benefits of using two-factor authentication (2FA) in crypto?
Here are some benefits of 2FA, essential in the crypto world:
- Added security layer: Passwords alone are easily hacked. 2FA adds another step, requiring a second verification beyond just your password, making it harder for unauthorised account access.
- Protection against hackers: Even if you lose access to the account when hackers obtain your password, they can't access your account without the second verification code from your authenticator app.
- Safer transactions: 2FA ensures that any attempt to move your crypto requires an extra verification code, making unauthorised transfers much more difficult.
- Widely available: Most crypto exchanges and crypto wallets offer 2FA. It's usually free and easy to set up, benefiting anyone holding cryptocurrency.
- Regulatory compliance: Some places require 2FA for crypto platform customer accounts.
📚Related: How to Stay Safe from Bitcoin Scams And Frauds
📚Related: How Fraudsters Exploit Social Engineering Tactics
What are the risks of not using two-factor authentication (2FA) in crypto
Unfortunately, skipping two-factor authentication (2FA) on your crypto accounts exposes them to several security risks:
- Missing security layer. Not using 2FA means missing out on an extra security measure that significantly protects your crypto assets. If your password is compromised, the absence of 2FA makes unauthorised access more likely.
- Possible unauthorised access. Without 2FA, there's a higher chance of unauthorised individuals gaining entry to your accounts, potentially leading to theft.
- Phishing vulnerability. Lack of 2FA makes users more susceptible to phishing attacks, where hackers trick them into giving up login details, providing easy access to compromised accounts.
- Hacking vulnerability. With only passwords for security, accounts are easier targets for hackers who can steal them through phishing or other methods.
While 2FA isn't foolproof, it adds a significant layer of security to your crypto holdings. It's generally considered essential for anyone investing in cryptocurrency.

Different methods of two-factor authentication (2FA)
Various methods of two-factor authentication (2FA) offer different levels of security and convenience:
SMS authentication
Users receive a one-time code via SMS messages to complete the login process. While widely accessible, this method is less secure due to vulnerabilities such as SIM swapping attacks and slow text delivery in areas with poor network coverage.
According to specialists, The most popular 2FA methods often rely on SMS verification because they're easy to use and work on all devices.
Email-based authentication
With email-based 2FA, users receive a one-time code to log in to their registered email address.
This method is straightforward. You can access your account from any device with internet access as long as you can access your email.
Biometric verification
Users authenticate using biometric identifiers. Biometric data has many unique points that are hard to copy. Many organisations see biometric authentication as one of the most secure ways to verify user identities.
While it is a powerful measure, it is as simple as activating a payment card on an iPhone using Face ID. You set up your fingerprint or face scan with your crypto account to make it work. When logging in, you still enter your password, but instead of a code, you use your fingerprint or face scan to confirm it's you.
Highly accurate and user-friendly, this method appeals to those who prefer not to remember multiple codes.

Mobile authentication apps
Mobile authentication apps, also known as 2FA or authenticator apps, are crucial for online security, especially with cryptocurrency.
Apps like Authy or Google Authenticator generate time-based, one-time codes for offline access. According to specialists, these apps offer two-step verification using algorithms like TOTP and HOTP after registration via SMS or voice.
The mobile authentication apps work offline and can be used with various mobile and web applications. They store a secret on the mobile phone needed for authentication, but this method is vulnerable to phishing attacks and secret extraction.
Moreover, while they offer higher security than SMS, this method requires initial setup and is tied to a specific device.
Hardware tokens
Hardware tokens, also called hard tokens, security keys, security tokens, or key fobs, are physical devices that boost login security by adding an extra layer of authentication beyond just a password.
Hardware tokens generate verification codes using methods like One-Time Passwords (OTPs) displayed on the screen or entering a PIN on the device. These enhance security and prevent unauthorised access to accounts and transactions.
Hardware tokens offer high security but come with a cost and the inconvenience of replacement if lost or damaged. Therefore, you still need to store it in a secure location.
Push notifications
Push notifications are sent to users' mobile devices when a login attempt is made. Users can accept or reject the request.
However, the proof-of-concept attack demonstrated that notification-based authentication systems have a high vulnerability rate of 82.2%, showing the risk of exploitation by hackers without needing to compromise smartphones.
This underscores the importance of using a multi-layered security approach, combining notification-based authentication with stronger methods like biometrics or hardware tokens, to enhance protection against advanced threats.
Backup codes
Backup codes are provided to users during setup as a contingency plan. If the primary 2FA method is unavailable, these codes can recover access to your accounts if your device is lost or the 2FA app is deleted.
📚Read more: How to Secure Your Crypto Wallet Effectively
How swissmoney leverages biometrics & two-factor authentication (2FA)
One of the methods used by swissmoney to secure your digital assets is a two-factor authentication (2FA).
Your account security
For the first login on a mobile device, you must complete 2FA. Initially, the app sends an SMS with a code to your mobile device. However, you can activate 2FA for enhanced security, requiring you to enter a code generated by the Google Authenticator app every time you log in.
After a successful login, the mobile device generates its private key, which is used to send requests to the server. A PIN or biometric is required for this to happen.
The mobile app and server communication is encrypted using HTTPS/TLS.
Overall, the 2FA method adds an extra layer of security to the login process, making gaining access to your account more difficult.
Biometrics for your convenience
For convenience and security, swissmoney offers biometric verification as an alternative to entering a session passcode each time you open the app. This single-factor method uses unique physical traits such as fingerprints or facial features to confirm your identity.

This approach provides a secure way to access your account without remembering a session passcode, which can be a more vulnerable authentication method.
Secure transaction verification
Additional confirmation is not required when transferring funds within your Swissmoney account, whether between wallets, IBANs, or cards or when making different transactions.
However, swissmoney requires 2FA for every external transaction to keep your funds safe.
In this scenario, your mobile device functions as the first factor (something you have), and your PIN/biometrics serve as the second verification factor (something you know/something that identifies you).
How do you set up your swissmoney app two-factor authentication (2FA)?
The steps to set up2FA on swissmoney app are quite simple:
Open the swissmoney app. From the Home page, go to your profile.

Tap ‘Security’.
Tap ‘Enable two-factor authenticator’.
Enter the code that you’ve received on your phone.
Here, you’ll see further instructions and your key. Copy the key. Be quick, as the session is 5 minutes long.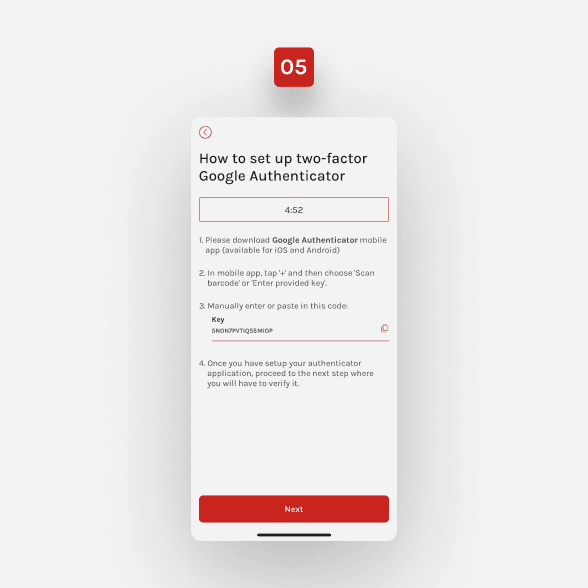
Download the Google Authenticator mobile app. Open the app and tap ‘+’.
Then, choose Other > Scan QR code > Or sign in manually.
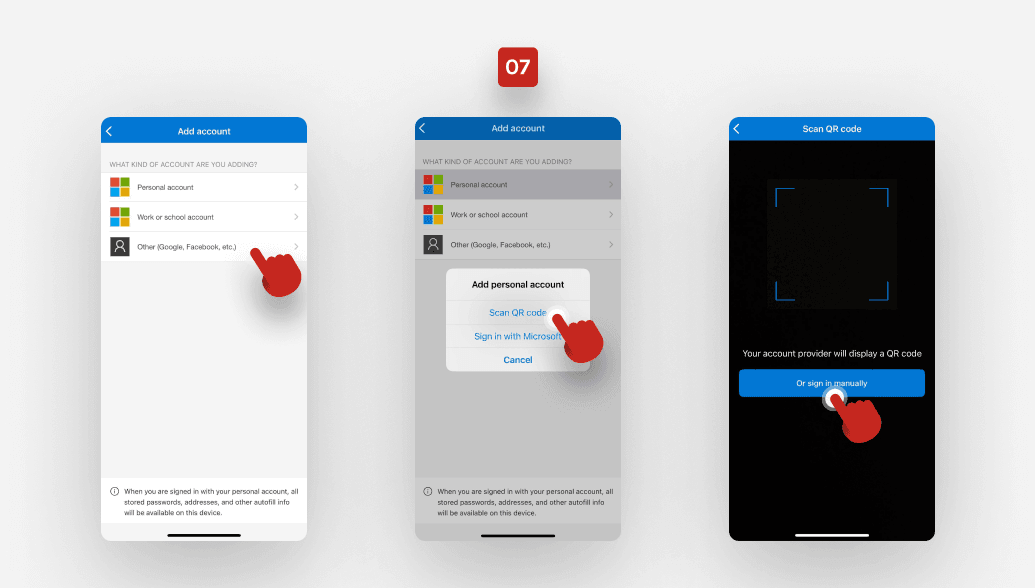
Enter the account name and paste the secret key.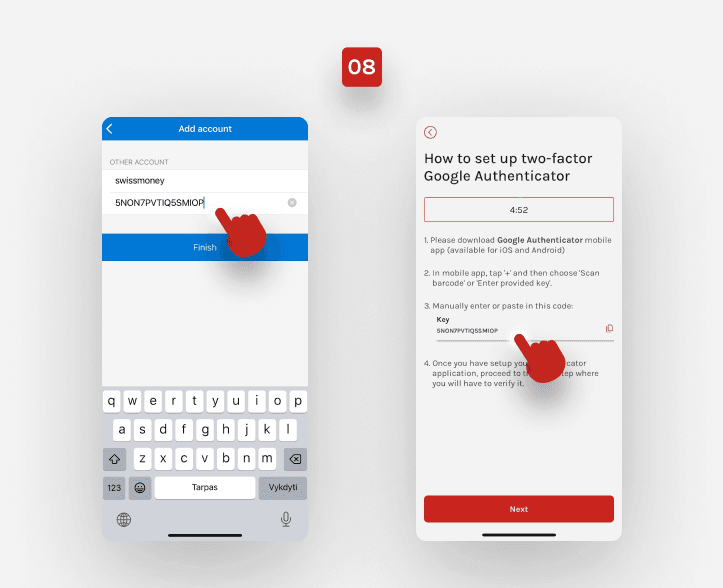
You’ll find the code on the main page of the Google Authenticator mobile app. Memorise it and be quick. The code expires in 30 seconds.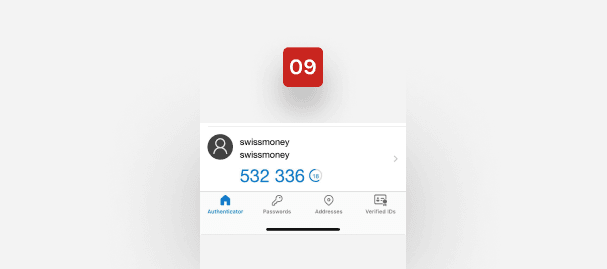
Click ‘Next’ and enter the code from Google Authenticator in 30 seconds.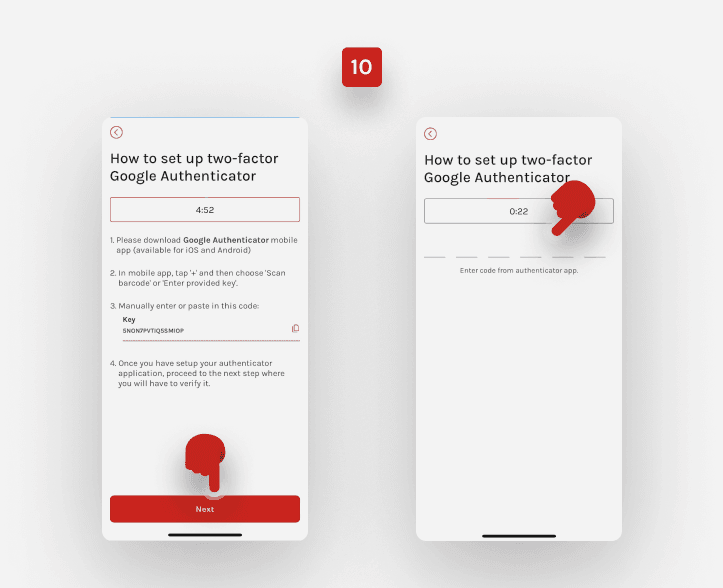
Now, every time you try to log in, you'll need to enter the code from Google Authenticator.
How do you set up biometric verification on the swissmoney app?
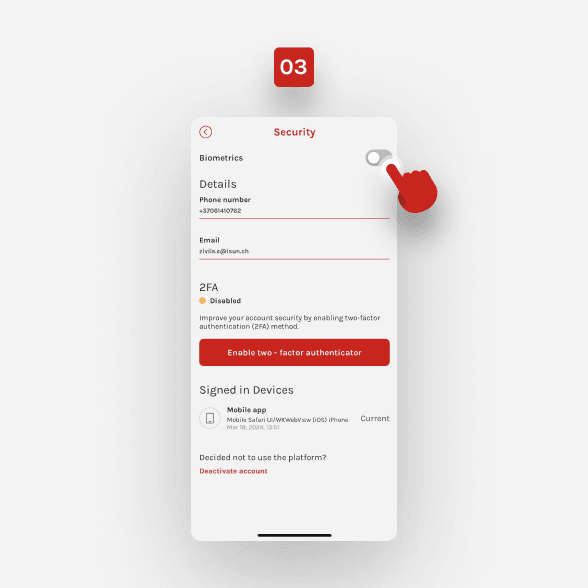
Open the swissmoney app. From the Home page, go to your profile.

Tap ‘Security’.

Tap a button beside ‘Biometrics’.
Conclusion
Two-factor authentication (2FA) in cryptocurrency is an important security measure. It requires both a password and another form of verification, like biometrics or a code.
This adds extra protection against unauthorised access and fraud. Biometric verification and hardware tokens are reliable options for 2FA. Choosing a secure authentication method is essential for safeguarding cryptocurrency transactions and accounts.
FAQs
What is 2FA for a crypto wallet?
Two-factor authentication (2FA) for a crypto wallet adds an extra layer of security by requiring two types of verification to access the crypto wallet. This helps stop unauthorised access.
The first verification is typically a password or PIN, while the second is a one-time code from an app or sent via SMS or email. This code changes with each login, making it harder for attackers to get in, even if they have the password.
What is the difference between biometric authentication and two-factor authentication?
2FA adds an extra security layer by needing two different authentication factors, while biometric authentication relies on one factor using unique biological traits.
Both methods enhance security compared to just using a password. However, they differ in convenience and the ability to replace compromised credentials.
What authenticator app should I use for Crypto?
Here are some popular and well-liked authenticator apps for crypto:
- Microsoft Authenticator: This is a free app with strong security features, including requiring hardware security keys for an extra layer of protection.
- Google Authenticator: A classic and reliable option, Google Authenticator is simple to use and generates time-based one-time passwords without needing an internet connection. However, it doesn't offer cloud backups or syncing across multiple devices.
- Authy (Twilio Authy): This app offers encrypted token storage, password protection, and optional cloud backups for added convenience. It's a popular choice with a good reputation.
Ultimately, the best authenticator app for you will depend on your needs and preferences.
However, when choosing an authenticator app, look for one with strong encryption, password protection, and multi-device support (if that is important to you). Also, ensure the app works with your phone's operating system and is easy to set up and navigate.
How do I get my crypto authenticator code?
You can't directly get your crypto authenticator code from your exchange or wallet. Instead, it's generated by your authenticator app and changes every 30 seconds for security.
Here's how it works:
- Set up 2FA: Enable two-factor authentication in your exchange or wallet settings and connect it to your authenticator app.
- Authenticator app generates code: Open your authenticator app to find the code, usually six digits long, for your exchange or wallet account.
- Enter code: Input the code from your authenticator app when prompted during login or transactions. Be fast; the code changes every 30 seconds.
Is biometric 2FA safe?
First of all, biometric login is considered a single "factor" for accessing your account, providing protection only on the device where you've set it up.
Still, biometric authentication is more secure than traditional password-based authentication, as biometric data is very difficult to replicate.
Is biometric authentication hackable?
Yes, biometric authentication can be hacked despite being seen as more secure than traditional passwords.
Hackers can exploit weaknesses in how biometric data is collected, processed, matched, and stored. They may use techniques like fake identities, deepfake technology, stealing biometrics, recreating them, bypassing checks, or social engineering to hack biometric systems.
What is the strongest authentication method?
Currently, two methods are competing for the title of the strongest authentication:
- Hardware security keys. These physical devices, often like USB sticks, create a unique code when used. They're highly secure because they must be physically held and can't be intercepted remotely.
- Biometric authentication. This method, also known as passwordless FIDO authentication, uses biometrics (like fingerprint or facial scans) or a secure key on your device to confirm your identity. It eliminates passwords completely, reducing a common security weakness.
Do hardware wallets have 2FA?
The idea of 2FA (two-factor authentication) isn't directly used with hardware wallets. They focus on securing your private keys and don't need passwords for basic tasks. Instead, they rely on physical confirmation actions on the device itself.
However, hardware wallets have features resembling 2FA:
- PIN security. You usually need to enter a PIN on the device to access your crypto, adding extra security beyond just having the device.
- Transaction confirmation. When you approve a transaction with a hardware wallet, you'll typically check the details (like amount and recipient) directly on the device screen. This ensures you know and agree to the transaction before it's done.
- FIDO U2F support. Some hardware wallets can work as FIDO U2F security keys. This means they can be a second verification factor for logging in to other online accounts, like a traditional 2FA app.
Read more

